Protect Yourself from Phishing Attacks
Have you set any New Year's resolutions for this year? How about improving your cyber protection? We will outline the most common signs of phishing attacks using an email example and discuss ways to protect yourself from it.
Written by human for humans
We all spend a lot of time online. The internet has become an integral part of our lives, a necessity for professional and personal activities. While there are numerous advantages to using the internet, it also comes with inherent dangers. Cybercriminals are constantly seeking opportunities to attack. Statistics show that a cyberattack happens every 39 seconds, and 95% of these incidents stem from human errors.

Cyberattacks have different motives, such as criminal, personal, or political, and come in various forms. Some of the most common types of cyberattacks are:
- Malware attacks: Malicious software that can cause disruption, harm or disable your computer, server, device, or network without you even knowing it. This category includes a range of attacks performed by malicious software such as spyware, ransomware, remote trojans, and computer worms.
- DDoS attacks (Distributed Denial of Service): This type of attack disrupts the information system by either causing malfunctions or overloading the system with information so it can no longer function effectively.
- Password attacks: Techniques like credential stuffing, guessing, brute force attacks, dictionary attacks, rainbow table attacks and others, are employed by attackers to crack passwords. Using strong passwords is crucial to protect yourself against such attacks.
- Social engineering: This involves manipulating and deceiving people to obtain confidential information or access to systems. It is an attack that exploits human characteristics such as trustworthiness and naivety.
What is phishing?
Phishing, a form of social engineering, is among the most prevalent cyber threats. This type of attack involves conniving tactics employed by cybercriminals to trick victims into revealing sensitive information such as credit card numbers or usernames and passwords for different online services, for example, bank accounts or PayPal accounts, social networks, etc. The attackers may even trick the victims into downloading malicious software onto their computers or phones.
Attackers usually use deceptive techniques through fake emails or private messages on different communication apps, often posing as legitimate companies or organizations. Typically, the victim receives a message (via SMS, email, or private message) urging them to click on an attached link.
These links may appear legit or contain slight spelling mistakes that are easily overlooked, leading individuals to fraudulent websites with deceptive data entry forms. If the victim enters their information on such fraudulent websites, it becomes accessible to attackers, putting the individual's sensitive data at significant risk. Additionally, phishing messages may include attachments, often carrying malicious software.

How to recognize phishing attacks?
We have created an example of an email phishing attack that includes typical signs of phishing attempts. While exaggerated, it serves to demonstrate what to watch out for.
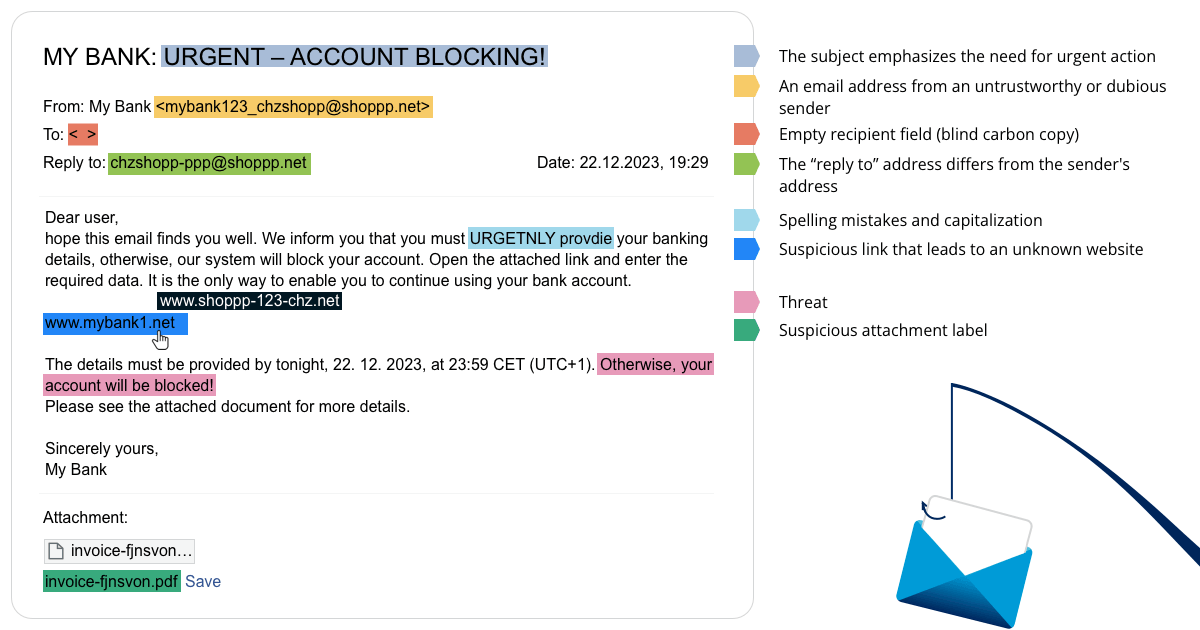
Email address
Always scrutinize the sender's email address. If you have any doubts, consider contacting the supposed sender, like your bank, directly through a verified phone number to confirm the email’s legitimacy before taking any further action. Even if the sender’s email address appears to be the official address of the alleged sender, it doesn't guarantee authenticity. Pay close attention to other potential signs of fraud within the message.
Be careful about emails appearing to be sent from official email addresses, such as those from the bank, the police, or even a friend. These emails may also give the impression of being sent from an official domain. In light of this, exercise extreme caution before responding to such messages, particularly when sharing personal information.
Recipient field
Check the recipient field of the message. An empty recipient field, indicating the use of blind carbon copy (bcc), is a common practice in mass messages, often associated with fraudulent activities.
Reply-to email address
Pay attention to the reply-to email address. If it differs from the sender’s address, be careful - it may be a sign of fraud.
An email subject line
Carefully examine the email subject line. Pay attention to the type of exclamation marks, incorrect language, spelling mistakes, or the use of urgent or threatening language. These elements may indicate the possibility of fraud.
Email content
Thoroughly review the content of the email. If the text is written unusually, contains spelling mistakes, or appears to be a poorly translated message from another language, it is likely a fraudulent communication.
Link in the email
If an email contains a link, always check it before opening it. If the link seems suspicious, visit the provider's official website to confirm whether the email includes a link to the authentic site. If you're uncertain about the domain, use one of the many available websites to verify it.
Where does the link redirect?
Always verify where the link redirects. Links may appear legitimate, but they can redirect to false websites. Hover your mouse over the link (without clicking on it), and the actual link will be revealed.
A threat
Typical phishing attacks include emails designed to prompt quick action, often accompanied by threats of unpleasant consequences if an immediate response is not provided.
An attachment
If a suspicious email contains an attachment, don't open it immediately. Even if the attachment appears to be a .pdf or .doc file, it doesn't guarantee security. Only open the attachment if you are absolutely sure it is not fraudulent.
It is worth noting that phishing emails typically contain only some of the mentioned signs simultaneously.
If you receive a strange, unexpected message, such as an email, possibly prompting you to provide personal data, pay attention to the individual signs outlined in the example.

SRC-EDIH
Koofr is a partner in the SRC-EDIH (Smart, Resilient, and Sustainable Communities – European Digital Innovation Hub) project, which supports the digital transformation of manufacturing companies and public organizations in Slovenia. The project focuses on five key technologies: HPC, artificial intelligence, cyber security, blockchain, and robotics. It is co-financed by the European Union and the Ministry of Digital Transformation of the Republic of Slovenia.
The material used in this blog post is part of the test environment we prepared for the project.

[Funded by the European Union. Views and opinions expressed are however those of the author(s) only and do not necessarily reflect those of the European Union or European Commission-EU. Neither the European Union nor the granting authority can be held responsible for them.]
Have you ever received a phishing message? Join the conversation in our Reddit community!


