How Two-Factor Authentication Improves Your Online Security
Adding an extra layer of verification beyond passwords is crucial for safeguarding personal information. Activate two-factor authentication on your online accounts today, starting with your Koofr cloud storage account, and contribute to a safer online environment.
Written by human for humans
[Learn more about securing your Koofr account with two-factor authentication.]
According to Surfshark’s statistics, almost 300M accounts were leaked in 2023, with Europe being the most breached region globally. 39% of all breached accounts were European. A single email address is breached approximately three times. Although data breaches have decreased from 2022 to 2023, being vigilant about your online security is still as important as ever. A way to do that is by practising safe online behaviour by using strong passwords, avoiding spam and phishing emails, and enabling two-factor authentication on all your online accounts.
Two-factor authentication is an extra measure you can use to secure your accounts. Instead of relying on your account password, two-factor authentication requires you to provide a second piece of information to verify your identity. There are three commonly acknowledged methods of authenticating yourself: knowledge (something you know), like a password, a possession (something you have), like a temporary code sent to your mobile device, or inherence (something you are), like, for example, a fingerprint or other biometric type of authentication. Two-factor authentication combines the password (something you know) with a second factor (something you have or something you are).
The purpose of two-factor authentication is to make it more difficult for unauthorized users to access your accounts even if they have your password. If someone manages to get ahold of your password, they will still need the second factor to gain access to your account, enhancing the security of your account.
1. How secure is your password-protected account?
As we increasingly rely on digital platforms and devices for various aspects of our lives, like communication, financial transactions, and personal information storage, online security becomes more and more important. As more sensitive data is transferred and stored online, the risk of unauthorized access to our accounts becomes higher and represents a significant concern.

Passwords are the first line of defence for our data, but that doesn’t mean people use strong passwords to secure their accounts. Check out if your password is on the list of the worst passwords from 2023.
Many people overlook the significance of strong passwords, making it easy for attackers to guess their passwords and gain unauthorized access to their accounts, but even the strongest passwords have limitations because they rely on only a single factor for authentication. In conclusion, passwords alone are not a sufficient method to secure our accounts. They are vulnerable to password attacks, such as brute-force attacks (attackers repeatedly trying different passwords), dictionary attacks (using common words or phrases as passwords), and credential stuffing (using leaked username and password pairs from other breaches).
Many users also tend to reuse passwords across multiple online accounts. If one of them is compromised, they all are at risk. Cybercriminals also rely on social engineering and tricking individuals into revealing their passwords with methods like phishing emails. As cyber threats evolve, the nature of passwords makes them less and less effective in keeping our accounts secure.
Two-factor authentication overcomes these limitations by introducing an additional security layer to our online accounts. It pairs the traditional password (something you know) with a second factor, significantly increasing account security and thwarting unauthorized access attempts. In an era of advancing technology and increasing cyber threats, multi-factor authentication has become indispensable for safeguarding sensitive data and preserving privacy.
2. Why should you use Two-Factor Authentication to secure your accounts?
As previously mentioned, while passwords serve as the first line of defence for your online accounts, two-factor authentication requires users to provide two pieces of information to verify their identity, before they can gain access to an online account. It adds a layer of verification and thus mitigates password vulnerabilities and adds additional protection to every online account.
Two-factor authentication is a way to address human error in online security. In cases of credential stuffing, where hackers use leaked username-password pairs from one service to gain access to other accounts where users have reused the compromised password, two-factor authentication helps prevent unauthorized access to those accounts.
In cases where users choose weak passwords or fall victim to phishing attacks, two-factor authentication acts as a safety net, helping ensure that your account stays protected since the second authentication factor is not that easy to come by.

Two-factor authentication is highly effective in preventing unauthorized login attempts, such as brute force attacks. Even if an attacker manages to crack your password, they will still need the second factor to access your account, significantly increasing the difficulty of unauthorized access. The second authentication factor is usually a dynamic, time-sensitive element, as opposed to usual static login credentials. Read more about it in the next paragraphs.
3. Different types of Two-Factor Authentication
Some common types of two-factor authentication are authentication apps, SMS (short message service) authentication and security keys. Authentication apps, like Google Authenticator and Authy, generate time-based one-time codes (TOTP) that users enter along with their passwords to gain access to their accounts. This is a very secure option since codes are time-sensitive and not transmitted, they can also work offline and do not need a mobile network to work. A drawback is the dependence on a single device, which can lead to a potential loss of access if the device is lost or reset.
With SMS authentication, the two-factor authentication codes are sent via text message to the user’s registered phone number. This is a widely used service that doesn’t require additional apps. Users are familiar with it, and it is simple. One disadvantage is its vulnerability to SIM swapping and interception, making it much less secure than authenticator apps and dependent on the mobile network.
Note: At Koofr, we prioritize the use of TOTP apps over SMS messages due to the higher security provided by time-based one-time codes and the avoidance of vulnerabilities associated with SMS-based authentication.
Another widely used method is authentication with security keys (for example YubiKey), hardware devices that users insert into their computers or tap for authentication. They are highly secure, resistant to phishing and convenient for users who prefer to own an authentication device. A downside is the expense associated with hardware, the potential lack of support on some platforms and services, and the risk of loss or damage.
4. Which Two-Factor Authentication methods you can use to secure your Koofr account?
Koofr is a cloud storage service that offers a comprehensive range of storage and file management services. Users can securely and privately store, organize, and share their files and documents through Koofr's user-friendly interface. Koofr cloud storage offers two different types of two-factor authentication to its users for increased security of their Koofr accounts.
You can either use Authentication apps or Time-based One-Time Passwords (TOTP) that generate temporary and unique codes which can be used as a second factor when logging into your Koofr account. Even if an unauthorized individual gains access to your username, password, and a single code, they must input the code within a limited timeframe, requiring real-time use.
Another option is to use a Passkey for two-factor authentication. While authentication apps are generally great at protecting your accounts, Passkeys take your account security a step further. When logging into your Koofr account, you have several different options of Passkeys you can use. A physical key (such as YubiKey) that connects to your device via USB or NFC, your biometrics (your fingerprint or face ID), your mobile devices, or your device’s PIN.
Koofr’s Passkeys rely on FIDO2 authentication. What is FIDO2? FIDO2 is an open authentication standard developed by the FIDO (Fast Identity Online). It aims to provide simpler and stronger authentication for online services, offering convenience and increasing online security.
Passkeys are more effective at preventing phishing attacks compared to Authentication apps. When you use a Passkey, it connects to the server and consistently verifies the domain you are accessing. This means Passkey only works on the sites and apps you linked it with, making it harder for phishing sites to trick you. For example, when logging in to your Koofr account, the Passkey ensures you are visiting https://app.koofr.net. While safe, Authentication apps only generate one-time codes without checking the website you are on for authenticity.
You can also turn on both options - verification with the Authentication app and a Passkey. This is a good option, in case one of the factors becomes unavailable - for example, you lose your passkey or your mobile device with the Authentication app.
5. How to turn on Two-Factor Authentication for your Koofr account?
You have two options for using two-factor authentication in your Koofr account. Either with the Authenticator app or with a Passkey.
If you are using the Authenticator app for two-factor authentication:
- In the first step, you need to download one of the TOTP apps to your device, for example Google Authenticator, Twilio Authy, or Microsoft Authenticator.
- Open the Koofr web app and click on Preferences in the Account menu.
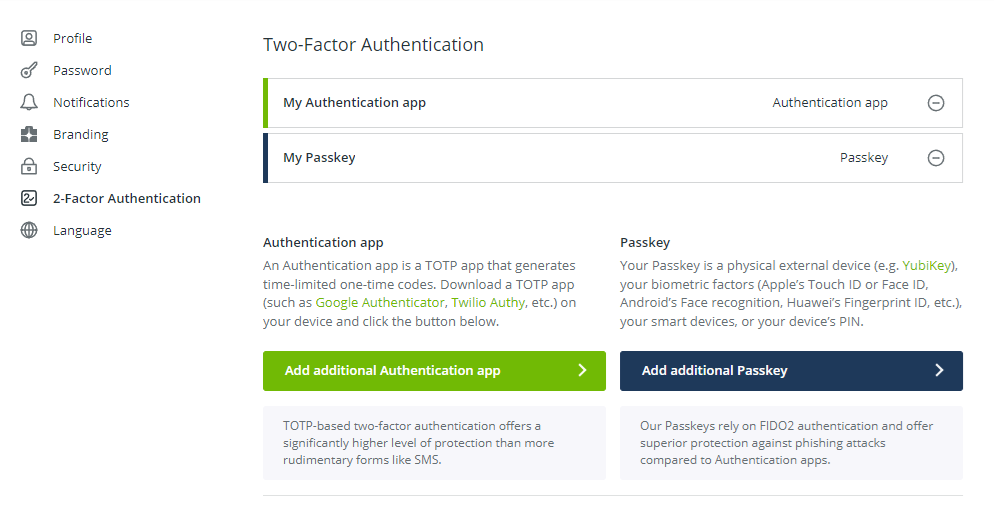
- In the left-side menu select 2-Factor Authentication and a screen like in the picture below will appear.
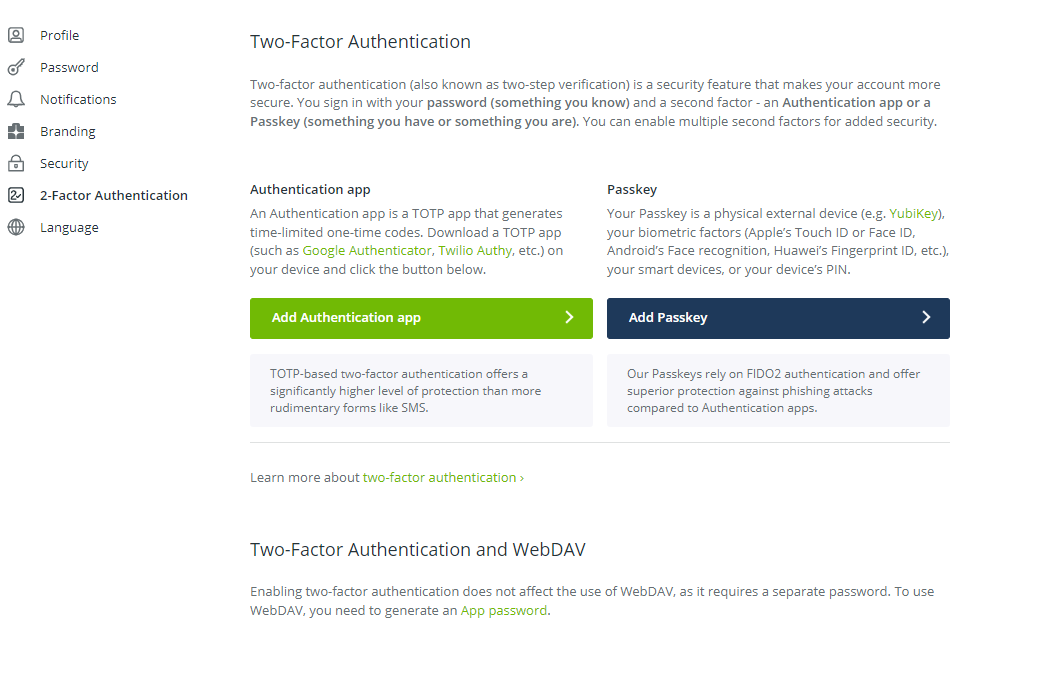
- Click on the Add Authentication app button to turn on two-factor authentication using the Authenticator app.
- Verify access to your Koofr account by typing your Password in the password field. Then click on Continue.
- Name your app and scan the offered barcode with your TOTP mobile app. If you cannot use a barcode, you can also enter an offered code.
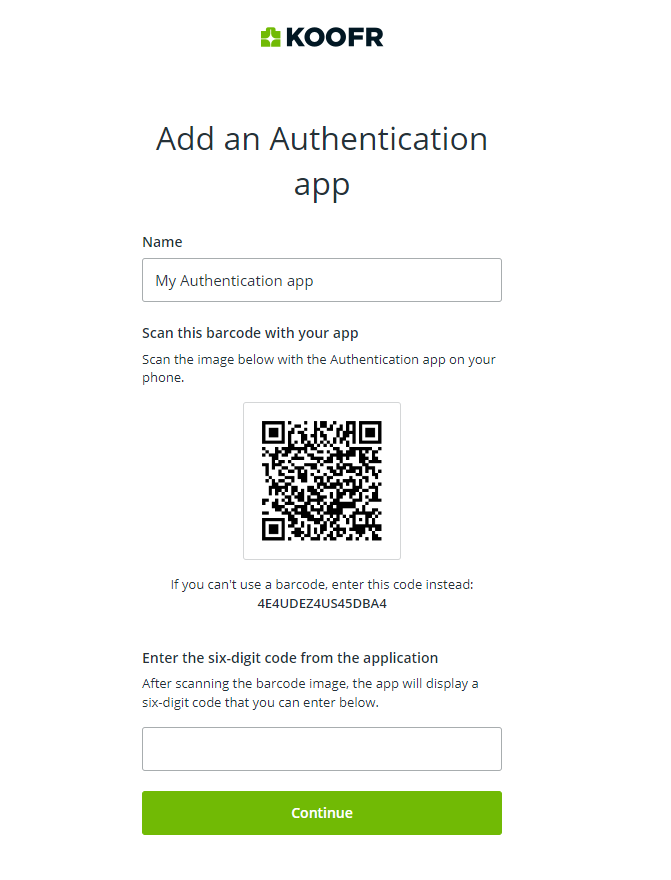
- Enter a six-digit code generated in your app and click on Continue.
- Save your two-step recovery codes in a safe place and click the Add button.
Note: If you experience issues with the code generated in your authenticator app, ensure that your device’s time is accurate. Time differences can disrupt TOTP authentication.
Note: Two-factor recovery codes must be stored in a safe place because they are the only way to restore your account if you lose your second factor. For example, if you lose your device with the Authentication app, and the Authentication app is your only enabled second factor, you can log in to Koofr using your recovery codes.
If you are using a Passkey for two-factor authentication:
- Open the Koofr web app and click on Preferences in the Account menu
- In the menu on the left, select 2-Factor Authentication
- Click on the Add Passkey button.

- Verify access to your Koofr account by typing your Password in the password field and clicking on Continue.
- Name your Passkey
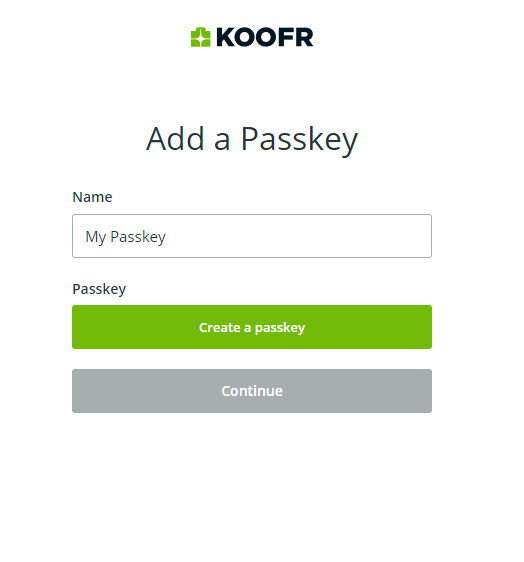
- Click on create a passkey and save it.
- Choose one of the supported FIDO authentication mechanisms.
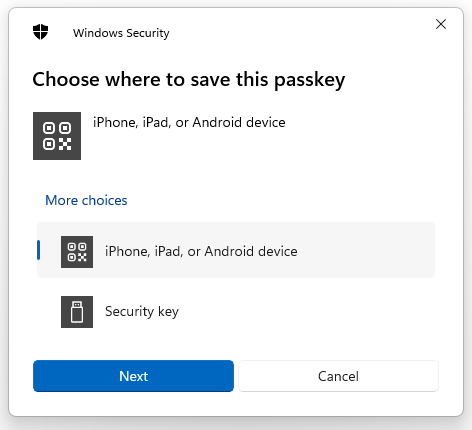
Note: This screenshot was made on Windows, but the options are fairly similar also on macOS, Android and iOS.
- Follow the provided instructions.
- Save your two-step recovery codes in a safe place.
Note: Two-factor recovery codes must be stored in a safe place because they are the only way to restore your account if you lose your second factor. For example, if you lose your Passkey and the Passkey is your only enabled second factor, you can log in to Koofr using your recovery codes.
- You will see the list of all your enabled second factors, such as Authentication apps or Passkeys, and have the option to add additional ones. Additionally, you can remove your connected Authentication app or Passkey.
Read more on our help pages.
In an era where online security is paramount and security concerns are heightened, two-factor authentication is a crucial tool for safeguarding personal and sensitive information. Adding an extra layer of verification beyond passwords significantly reduces the risk of unauthorized access to online accounts, protecting users from various cyber threats such as phishing, password breaches, and unauthorized login attempts.
Taking proactive measures is essential to elevate your online security. Start by activating Two-Factor Authentication across all your accounts, beginning with your Koofr cloud storage account. By doing so, you not only enhance the protection of your data but also contribute to a safer online environment. Embrace the heightened security that two-factor authentication offers and establish it as a routine practice to fortify your accounts against potential threats.
Do you already use two-factor authentication for your online accounts? Join us on the Koofr subreddit and discuss different two-factor authentication methods!


